14.6 Overview of Access Control List Management for Oracle Directory Objects
Identifies the security groups specific to Oracle directory objects within Active Directory and explains how to add and delete security group members.
Topics:
- Overview of Security Groups
Security groups are automatically created when the Oracle Context is created in Active Directory. - Setting ACLs on Net Service Entries
Use the MicrosoftDsacls.exetool to set ACLs on directory objects. - Adding and Deleting Security Group Members
Learn how to add or remove users in the security groups with Active Directory Users and Computers.
14.6.1 Overview of Security Groups
Security groups are automatically created when the Oracle Context is created in Active Directory.
The user configuring access (and thus creating the Oracle Context) is automatically added to each group.
Topics:
- About OracleDBCreators
TheOracleDBCreatorsgroup is for the person registering the Oracle Database server. - About OracleNetAdmins
Describes the various tasks that the users in this group can perform. - About Oracle Net Services Objects
In Oracle Database Client 11g or later, directory clients may optionally be configured to authenticate with the directory while resolving DB names to connect strings.
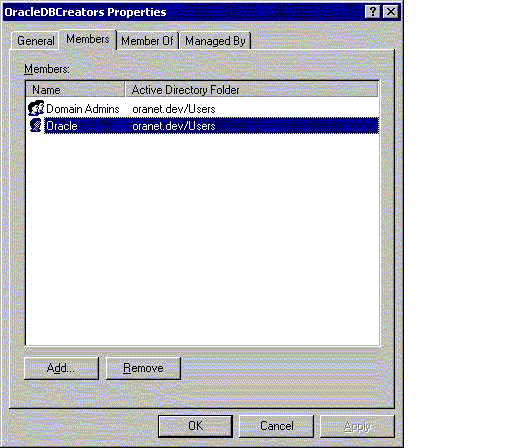
14.6.1.1 About OracleDBCreators
The OracleDBCreators group is for the person registering the Oracle Database server.
The domain administrator is automatically a member of this group. Users in this group can:
-
Create new Oracle Database objects in the Oracle Context.
-
Modify the Oracle Database objects that they create.
-
Read, but not modify, the membership for this group.
14.6.1.2 About OracleNetAdmins
Describes the various tasks that the users in this group can perform.
Users in the OracleNetAdmins group can:
-
Create, modify, and read Oracle Net Services objects and attributes.
-
Read the group membership of this group.
14.6.1.3 About Oracle Net Services Objects
In Oracle Database Client 11g or later, directory clients may optionally be configured to authenticate with the directory while resolving DB names to connect strings.
This makes it possible for Oracle Net Services objects to be protected using ACLs.
There are many ways in which the identities of users may be defined in the directory, and how those users or certain groups of users may be given access to some or all Net Services. Oracle Database supplies no predefined groups, and has no procedures in the config tools for defining read-access restrictions on this data. Therefore, administrators must use standard object management tools from their directory system to manually create any necessary groups and ACLs. Existing identity structures may be referred to by Net Service ACLs.
The access definitions for objects are complex and may involve security properties which are inherited from parent nodes in the Directory Information Tree (DIT).
Oracle recommends that the administrators should refer to the relevant tools and documentation for the directory system they are using, and formulate or integrate access management for Oracle Net Services objects into a directory-wide policy and security implementation.
Note:
Pre-11g clients can only bind to the directory as anonymous, so any ACL protection on Net Services disables older clients. Access Control can only be implemented if all clients requiring access to these objects are 11g or later.
14.6.2 Setting ACLs on Net Service Entries
Use the Microsoft Dsacls.exe tool to set ACLs on directory objects.
The Dsacls.exe command-line tool displays and changes permissions (access control entries) in the Access Control List (ACL) of objects in Active Directory. This command-line tool is included with the support tools on the CD-ROM.
Examples:
To enable an anonymous generic read on the orcl service, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /G "anonymous logon":GR
To enable a generic read on the orcl service for the user smith in the EXAMPLE domain, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /G example\smith:GR
To disable an anonymous generic read on the orcl service, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /R "anonymous logon"
To disable a generic read on the orcl service for the user smith in the EXAMPLE domain, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=com" /R example\smith
See Also:
http://support.microsoft.com/kb/281146 for a complete description of the Dsacls.exe tool
14.6.3 Adding and Deleting Security Group Members
Learn how to add or remove users in the security groups with Active Directory Users and Computers.
You can add or remove users in the security groups with Active Directory Users and Computers.
Note:
Use Active Directory Users and Computers to perform the procedures described in this section. Windows Explorer does not provide the necessary functionality.
To add or remove users: